MetaCTF 留档
解出的题目
Interception I (100 pts) (Other)
192.168.0.1 is periodically (once every 4 seconds) sending the flag to 192.168.0.2 over UDP port 8000. Go get it.
ssh ctf-1@host.cg21.metaproblems.com -p 7000
ssh 连接到对面主机,给了一个 BusyBox 环境。
可以去 /usr/bin 和 /usr/sbin 下看看有什么能用的网络工具,发现了这些玩意:
- ifconfig
- netstat
- nc
- nmap
- tcpdump
- telnet
- arping
根据题意,考虑通过 ARP 欺骗,顶替 192.168.0.2,从而获取数据包。在终端下运行如下命令:
1 | ifconfig eth0 192.168.0.2 netmask 255.255.255.0 |
然后 ping 一下网关,更新一下 ARP 映射表,nc 监听 8000/udp 即可获取 flag。
Interception II (150 pts) (Other)
Someone on this network is periodically sending the flag to … someone else on this network, over TCP port 8000. Go get it.
ssh ctf-46ed3559da08@host.cg21.metaproblems.com -p 7000
我们的目标和 Interception I 相同,但这次我们不知道 src 和 dst IP 了。
知道端口号,还有 nmap,考虑扫描整个网段内的所有 IP 地址,获取存活主机的信息。
1 | nmap -p 8000 192.168.0.0-255 |
扫出来只有 192.168.0.78 的 TCP 8000 端口开着,和上面一题一样,直接把它挤掉。
1 | ifconfig eth0 192.168.0.78 netmask 255.255.255.0 |
用 nc 监听自己的 8000/tcp 即可获得 flag。
Easy as it (TCP) Streams (250 pts) (Forensics)
Caleb was designing a problem for MetaCTF where the flag would be in the telnet plaintext. Unfortunately, he accidentally stopped the packet capture right before the flag was supposed to be revealed. Can you still find the flag? Note: You’ll need to decrypt in CyberChef rather than using a command line utility.
下载下来一个 pcap 文件,用 Wireshark 打开,按照套路,先追踪一下 TCP 流。
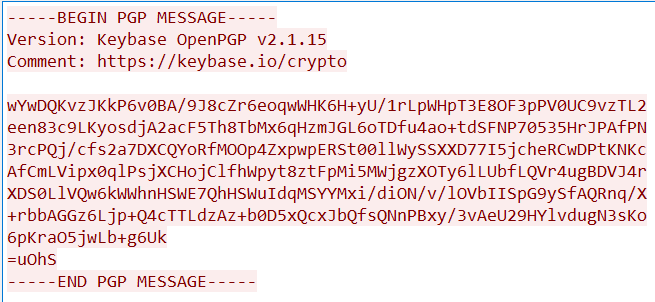
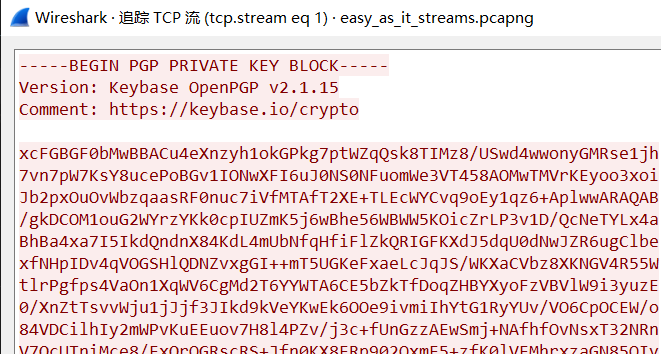
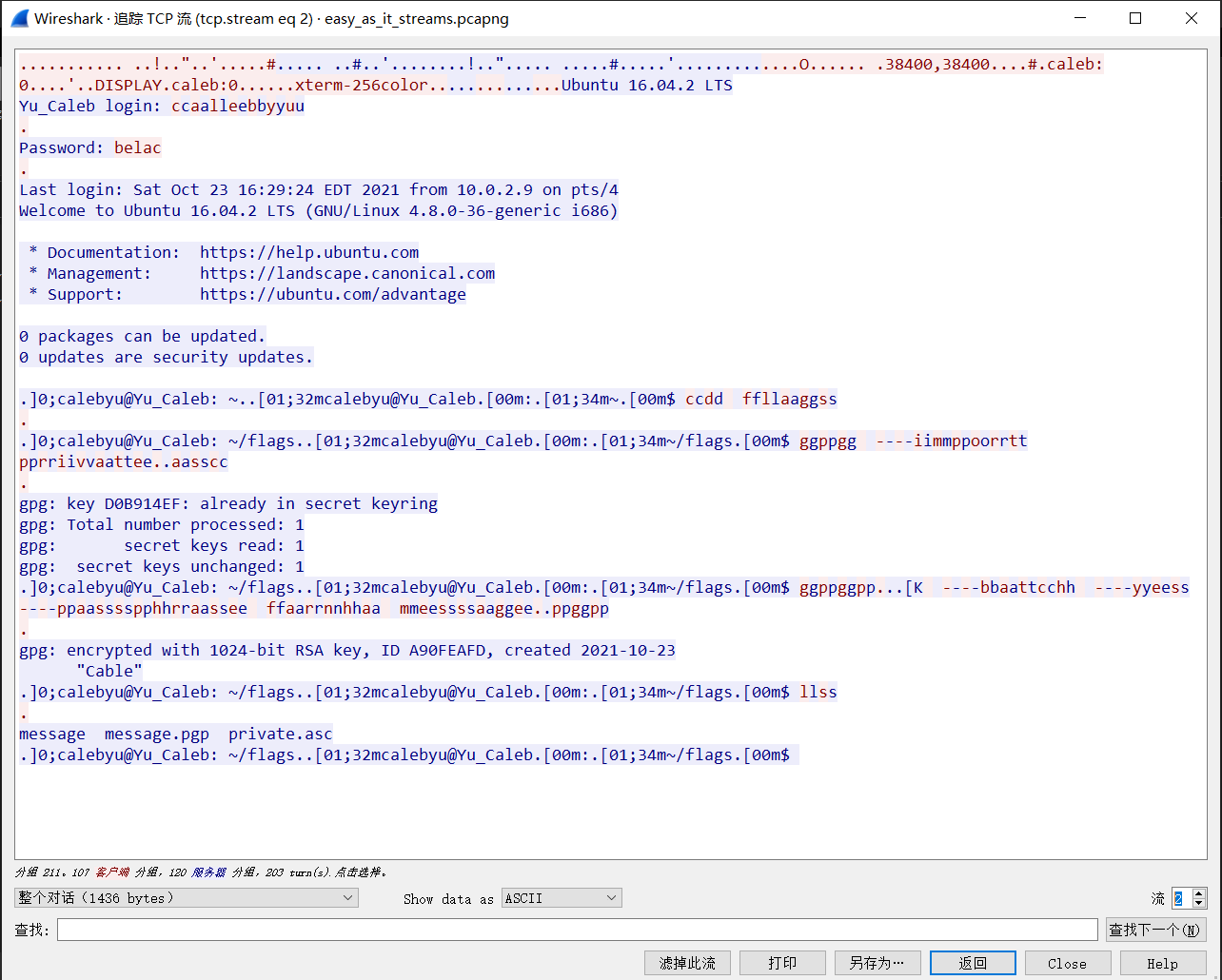
看起来主机用 gpg 加密了一个文件,流 0 有 PGP Message,流 1 有 PGP Private Key,流 2 有 passphrase。扔到 CyberChef 里可以一把梭。
Pattern of Life (275 pts) (Forensics)
Hackers have breached our network. We know they are there, hiding in the shadows as users continue to browse the web like normal. As a threat hunter, your job is to constantly be searching our environment for any signs of malicious behavior.
Today you just received a packet capture (pcap) from a user’s workstation. We think that an attacker may have compromised the user’s machine and that the computer is beaconing out to their command and control (C2) server. Based on some other logs, we also think the attacker was not using a fully encrypted protocol and also did not put much care into making their C2 server look like a normal website. Your task? We’d like you to submit the port number that the C2 server is listening on in the form of MetaCTF{portnumber} as the flag.
下载下来一个 pcap 文件,用 Wireshark 打开。题目要求是找到本机被监听的端口,给的提示有两个:
- 用的不是加密协议
- 看起来很可疑(异常流量?)
流太多了,显然不能直接看。想到这个用户可能在疯狂浏览网页,而现在 HTTPS 在国外覆盖率很高,不妨把 443 端口直接无视掉?
结果喜人,流量一下少了一大半,从上往下翻,发现本机的 8080 端口十分可疑,从头到尾都在疯狂地与对面主机的 49694 端口你来我往。答案也正是 8080。
I want my files back (275 pts) (Reconnaissance)
While the world continues to battle COVID-19, the digital world continues to battle its own epidemic - ransomware. Criminals continue to hold organizations’ files hostage as they cast a wide net hacking anyone with a vulnerable device or through phishing.
Fortunately criminals aren’t always the sharpest tool in the shed, and sometimes it’s possible to decrypt a ransomwared file without paying the ransom. We’ve come across one such file - perhaps you can figure out what Ransomware strain encrypted it and a way to decrypt it?
There have been problems with downloading the entire file on Firefox, the md5sum of the file is 32cbeca49de4e1b297550f4ae95a39b6
下载附件,给了一个被勒索文件加密的 png 文件,要求是解密。
- 文件名有 [AA4-MX4-GGQD] 字样
- 010 Editor 打开,看到末尾有 GotAllDone 字样
谷歌可知,勒索软件叫做 Prometheus。
GitHub 找到一个可以解密这玩意的 Python 脚本,功能貌似还挺强大,支持 GUI,支持通过特征字节缩小密码范围。
https://github.com/cycraft-corp/Prometheus-Decryptor
下载、爆破,打开图片就是 flag。
The Searcher (275 pts) (Reconnaissance)
Alright analyst. We need your help with some investigative work as we dive deeper into one of the infections on our company’s network. We’ve taken a small packet capture that we know contains some C2 traffic. In order to give us some more leads for the investigation though, we’d like to see if we can identify what C2 framework the attacker was using. This will give us some leads into potential host-based artifacts that might be left behind.
Please submit the name of the C2 Framework being used in the form of MetaCTF{c2frameworkname}
又双叒下载下来一个 pcap 文件,用 Wireshark 打开。
追踪流可以看到几个有意思的东西,其中最有意思的当属这个。
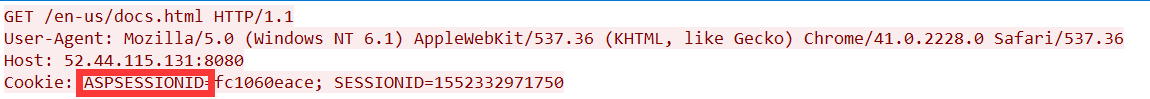
ASP.NET?
Google 搜索 C2 Framework ASP.NET 可以搜到 Covenant,交上去就是 flag。
未解出的题目
Interception III (275 pts) (Other)
当时不懂路由(
进入环境之后,telnet 本地网关,在 enp0s0 设备上再加一个目标 IP 实现 ARP 欺骗。
然后 nc 监听自己的 8000/udp 即可获得 flag。
Mystery C2 Server (350 pts) (Reconnaissance)
To do…
The Carver (475 pts) (Forensics)
To do…
Where’s Vedder? (525 pts) (Reconnaissance)
Vedder 三部曲的第一部,分值高得吓人。
翻了题解,实在没看出来那个房子是 Funeral House……
这就是文化差异吗?
知道是 Funeral House 之后,全州筛查「在公共森林中心的 Funeral House」即可。
Online Presence (550 pts) (Reconnaissance)
To do…
They call me TracerT (550 pts) (Reconnaissance)
To do…
New Spot (600 pts) (Reconnaissance)
To do…
Step into the NET (600 pts) (Other)
To do…
按照题目描述来看,是道综合型的取证分析题目。
